Secure IoT Remote Access: SSH, VPN & More - Your Ultimate Guide!
In a world increasingly defined by interconnected devices, is it truly possible to monitor and manage your Internet of Things (IoT) devices from virtually anywhere? The answer, unequivocally, is yes, and the key lies in secure remote access.
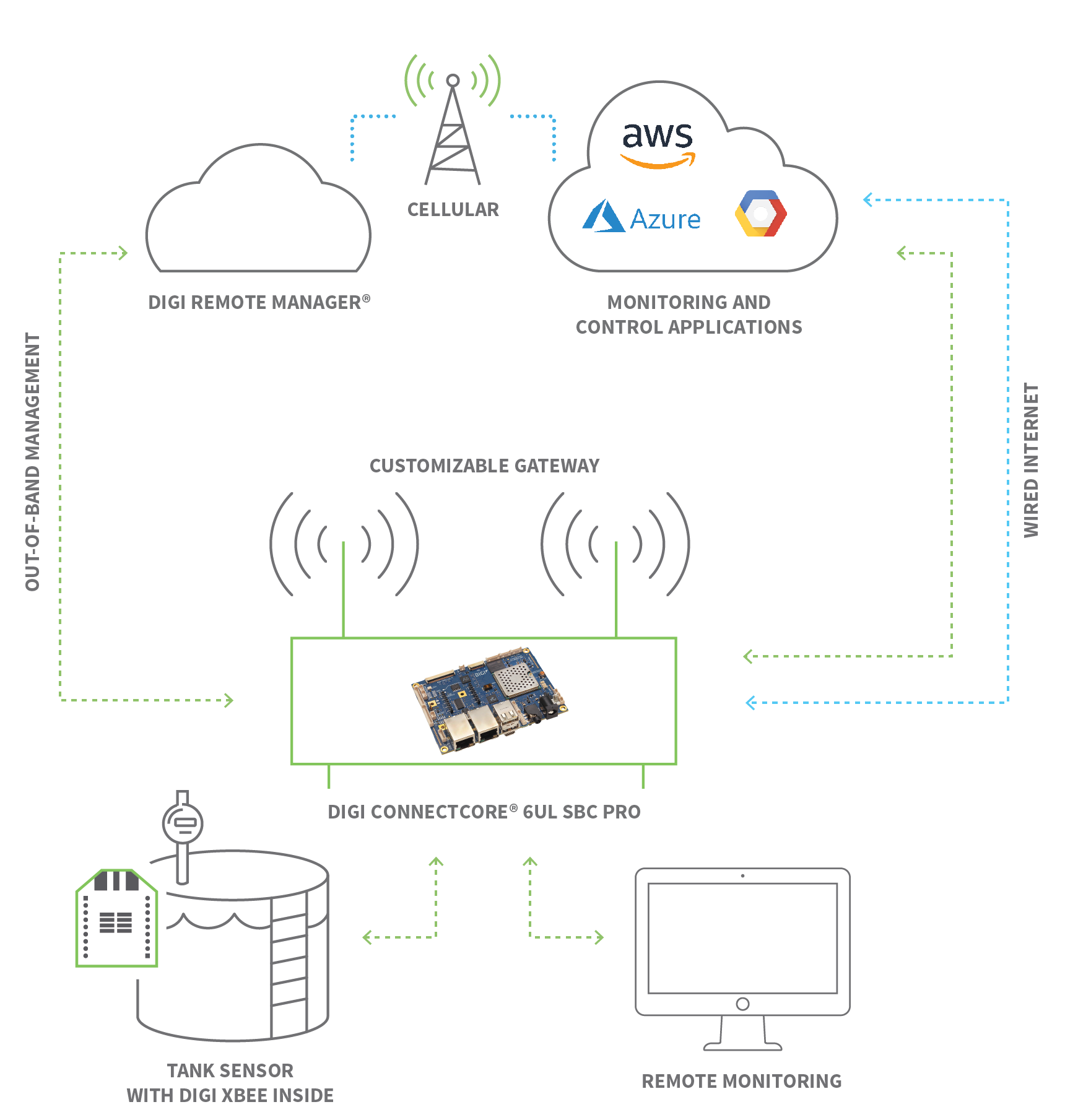
The ability to remotely access and control IoT devices is rapidly becoming a cornerstone of modern technology. Whether it's optimizing industrial processes, managing smart homes, or overseeing complex networks of sensors, the benefits are undeniable. This article delves into the intricacies of establishing secure remote connections, exploring the methods, protocols, and tools that empower users to seamlessly manage their IoT infrastructure from any location. We'll examine the importance of robust security, provide step-by-step guides, and illuminate the practical applications that make remote access an indispensable feature in today's connected world. The goal is to equip you with the knowledge and confidence to harness the full potential of your IoT devices, regardless of your physical location.
Imagine the possibilities: controlling your smart home's lighting, temperature, and security systems while on vacation, or troubleshooting industrial equipment from a remote office, saving time and resources. Remote access isn't just a convenience; its a necessity. It allows for real-time monitoring, proactive maintenance, and efficient problem-solving, ensuring that your IoT devices operate optimally and reliably.
- Carly Jane Onlyfans Leak A Critical Look At Privacy Content Risks
- Miya Melody Onlyfans Leaks Hot Content Videos
The landscape of remote access for IoT devices is diverse, encompassing a range of technologies and protocols, each with its strengths and specific use cases. The Secure Shell (SSH) protocol, known for its robust encryption, provides a secure channel for accessing devices, making it a popular choice. Virtual Network Computing (VNC) offers a graphical interface, mirroring the device's screen and enabling interactive control, while Remote Desktop Protocol (RDP) offers a similar experience, commonly used in Windows environments. For secure tunneling, services like pinggy.io can be utilized, creating protected pathways for remote management, bypassing the need for complex port forwarding configurations.
The following table provides key information about the leading methods for remotely accessing and managing IoT devices:
| Method | Description | Key Features | Pros | Cons |
|---|---|---|---|---|
| SSH (Secure Shell) | A cryptographic network protocol for secure remote access to a computer or server. | Secure terminal access, file transfer, port forwarding. | High level of security, widely supported, efficient for command-line access. | Primarily command-line based, less user-friendly for graphical interfaces. |
| VNC (Virtual Network Computing) | A graphical desktop sharing system that uses the RFB protocol to remotely control another computer. | Graphical interface access, screen sharing, remote control. | Easy to set up, provides a visual interface, cross-platform compatibility. | Can be bandwidth-intensive, security depends on configuration, potential latency issues. |
| RDP (Remote Desktop Protocol) | A proprietary protocol developed by Microsoft for remote access to a desktop environment. | Graphical interface access, screen sharing, remote control. | Optimized for Windows environments, good performance, integrates well with Windows. | Primarily for Windows systems, requires specific licensing in some cases, may have security concerns if not properly configured. |
| VPN (Virtual Private Network) | A secure connection over a public network, creating a private network environment. | Secure tunneling, encryption, IP address masking, access to private networks. | High level of security, access to entire network, good for sensitive data transmission. | Requires configuration, can introduce latency, needs a VPN server. |
| pinggy.io (Secure Tunnels) | A service that allows creating secure tunnels to expose local servers to the internet. | Easy port forwarding, secure connections, no need for public IP. | Simple setup, bypasses firewall and NAT issues, good for testing and development. | May have bandwidth limitations, depends on the service's availability. |
The Secure Shell (SSH) protocol stands out as a particularly robust choice for remotely accessing IoT devices, primarily because of its emphasis on encryption throughout the server connection process. SSH creates a secure channel, encrypting all data transmitted between the remote device and the accessing machine. This encryption is crucial for protecting sensitive information from interception, which is a paramount concern in any IoT deployment. SSH ensures the confidentiality and integrity of the communication, which makes it a preferred method for command-line access and secure file transfers.
Consider a scenario where you manage a fleet of industrial sensors. Using SSH, you can remotely connect to each sensor, monitor its data streams, and execute commands to adjust its configuration or update its firmware. All of this occurs within a secure, encrypted environment. This capability is particularly valuable in settings where devices are spread across different geographical locations and where maintaining data security is critical. You can securely connect to your Raspberry Pi or any other IoT device remotely over the internet, eliminating the need for complex port forwarding configurations.
VNC (Virtual Network Computing) and RDP (Remote Desktop Protocol) offer different approach, they provides a graphical interface, mirroring the device's screen on your remote computer. With VNC, you can view and interact with the device's desktop, run applications, and troubleshoot issues in real time. VNC is particularly useful when you need to visually monitor an interface or troubleshoot configuration issues. The flexibility and control it provides makes it a great choice for many IoT management scenarios. However, while offering ease of use, it is crucial to consider the security implications. Always ensure VNC is properly configured with strong passwords and encryption to protect against unauthorized access.
RDP, primarily used in Windows environments, offers a similar experience. Its performance is often optimized for Windows systems. When deployed correctly, it can offer a seamless remote desktop experience. While RDP is a powerful option, it also requires careful attention to security. Always implement appropriate security measures, such as strong passwords and up-to-date security patches. Furthermore, limiting the IoT device's open ports, permitting only necessary connections, is vital for enhancing security. Typically, this means permitting only port 5901 for VNC or the specific port used by RDP.
Virtual Private Networks (VPNs) further enhance security. A VPN creates a secure tunnel over a public network, providing a private connection between the accessing computer and the IoT device, especially when those devices are behind firewalls or private networks. This added layer of security is crucial in professional and industrial settings where data sensitivity is high, or when direct remote access is essential. The use of VPNs protects data in transit, providing an encrypted pathway and masking the user's IP address, further safeguarding sensitive data.
Tools like pinggy.io provide an alternative approach, especially useful for bypassing the complexities of port forwarding. Pinggy.io creates secure tunnels to expose local servers to the internet, simplifying remote access. This can be incredibly useful for quickly accessing devices without the need to modify the network's firewall settings or configure port forwarding rules. While these tools can be extremely convenient, always assess the security measures and be mindful of potential bandwidth limitations.
Setting up remote access for your IoT devices may vary based on the device and manufacturer. Generally, it involves these steps: first check compatibility and firmware updates, then install remote access tools and configure network settings (including port forwarding or VPN setup), and finally, test the connection. Many manufacturers provide companion applications or software that simplifies this process. If direct methods are used for management, like modifying the behavior of devices connected to your IoT hub, be sure to use secure protocols and authentication to prevent unauthorized access.
After setting up the necessary tools, you can remotely SSH to your IoT devices with just a few clicks. This makes it easy to make quick changes or monitor your devices when you're on the go. Moreover, ensure that your IoT devices are compatible with remote access protocols and that they have the required firmware and software to support remote control. The remote access capability is crucial for managing and supporting a wide array of IoT devices, such as smart appliances, industrial sensors, and connected vehicles.
The benefits of implementing remote access to your IoT devices are numerous. It simplifies and streamlines the management of IoT devices at scale, improving operational efficiency and reducing risks. Remote access solutions enable businesses to react quickly to changes and issues that are occurring with IoT devices remotely, from anywhere, allowing quick troubleshooting, configuration and updates. This can also contribute to reduced downtime and improved efficiency.
For enterprises, remote access to IoT devices unlocks substantial advantages. Consider, for instance, the logistics sector. The ability to remotely monitor and manage assets, such as connected vehicles or warehouse sensors, optimizes operations, enhances supply chain visibility, and facilitates real-time decision-making. This translates to improved efficiency, reduced costs, and greater responsiveness to customer needs. A newly conducted study forecasts substantial growth in the deployment of IoT technology in the global supply chain market, projected to grow at a Compound Annual Growth Rate (CAGR) of 13.2 percent between 2020 and 2030. This growth underscores the increasing importance of secure and efficient remote access solutions.
Furthermore, the remote access enhances the ability of businesses to perform regular maintenance. By leveraging these capabilities, businesses can proactively identify and address issues before they escalate, minimizing downtime and ensuring optimal performance. It enables swift intervention and repair, regardless of the location of the device. This proactive approach minimizes service interruptions and maintains the devices in a reliable state. Efficient and reliable support has become a cornerstone of a strong customer experience, enabling IoT businesses to resolve problems rapidly and keep their customers satisfied.
The Internet of Things (IoT) device management is a list of processes, including equipping, validation, configuration, monitoring, and analysis of connected devices in an IoT environment, which aim to support their functions. An effective and secure IoT device management solution is highly vital for the smooth and secure functioning of IoT devices. This is why securing remote access to IoT devices is essential for maximizing their functionality while maintaining a strong security posture. The goal is to ensure that IoT devices can be accessed and managed securely from any location.
SocketXP offers a platform to remotely connect to any IoT device behind a NAT router and firewall. This makes remote access even more accessible by removing the need for complex network configurations. By implementing these methods, you transform your IoT network into a conduit of seamless productivity. Securing remote access also means maximizing their functionality while maintaining a robust security posture.
In summary, the ability to securely connect to and manage your IoT devices remotely is a fundamental aspect of modern IoT management. From the robust encryption of SSH to the graphical flexibility of VNC and the security of VPNs, various methods are available, and each caters to different needs. By understanding the benefits of remote access, implementing proper security measures, and utilizing the available tools, you can unlock the full potential of your IoT devices and optimize their operation, regardless of your location. Your ability to access and control these devices empowers you to be more efficient, more responsive, and more in control of your connected environment. Always remember to prioritize security and consider the specific needs of your devices, networks, and applications to ensure a smooth and secure remote access experience.
Article Recommendations


Detail Author:
- Name : Dr. Richard D'Amore Sr.
- Username : rory61
- Email : lkovacek@kreiger.com
- Birthdate : 2000-07-08
- Address : 1759 Mavis Stream Apt. 974 New Katherine, NH 54042
- Phone : +16068138629
- Company : Ruecker Group
- Job : Personal Home Care Aide
- Bio : Excepturi consequatur architecto fuga culpa quae ut. Ut minus placeat placeat quidem. Adipisci eos molestias quia ab.
Socials
linkedin:
- url : https://linkedin.com/in/concepcion_zemlak
- username : concepcion_zemlak
- bio : Mollitia velit consequuntur reiciendis quidem.
- followers : 5944
- following : 367
facebook:
- url : https://facebook.com/concepcionzemlak
- username : concepcionzemlak
- bio : Rerum laboriosam consectetur sunt id id.
- followers : 6813
- following : 682
tiktok:
- url : https://tiktok.com/@czemlak
- username : czemlak
- bio : Natus odio optio ullam illum omnis excepturi officia.
- followers : 6068
- following : 1970
twitter:
- url : https://twitter.com/concepcion_zemlak
- username : concepcion_zemlak
- bio : Ipsum error sint repellendus. Amet eum error voluptatem distinctio voluptatem. Vel deserunt aut nam dignissimos rerum aut debitis eos.
- followers : 3096
- following : 1361
instagram:
- url : https://instagram.com/concepcion_dev
- username : concepcion_dev
- bio : Eos rem ad ullam cumque ad quis. Qui ullam molestiae facilis corporis est eum. Quia sint qui ullam.
- followers : 539
- following : 1693