Remote IoT Access: A Guide To Secure Connections & Setup
Can you truly control your world from anywhere? The rise of remote access to Internet of Things (IoT) devices has made this dream a tangible reality, offering unprecedented control and flexibility.
The ability to remotely access and manage IoT devices is rapidly transforming industries and everyday life. From adjusting the thermostat in your home to monitoring complex industrial machinery, the potential applications are vast. But how does this technology work, and what are the key considerations for implementing it effectively?
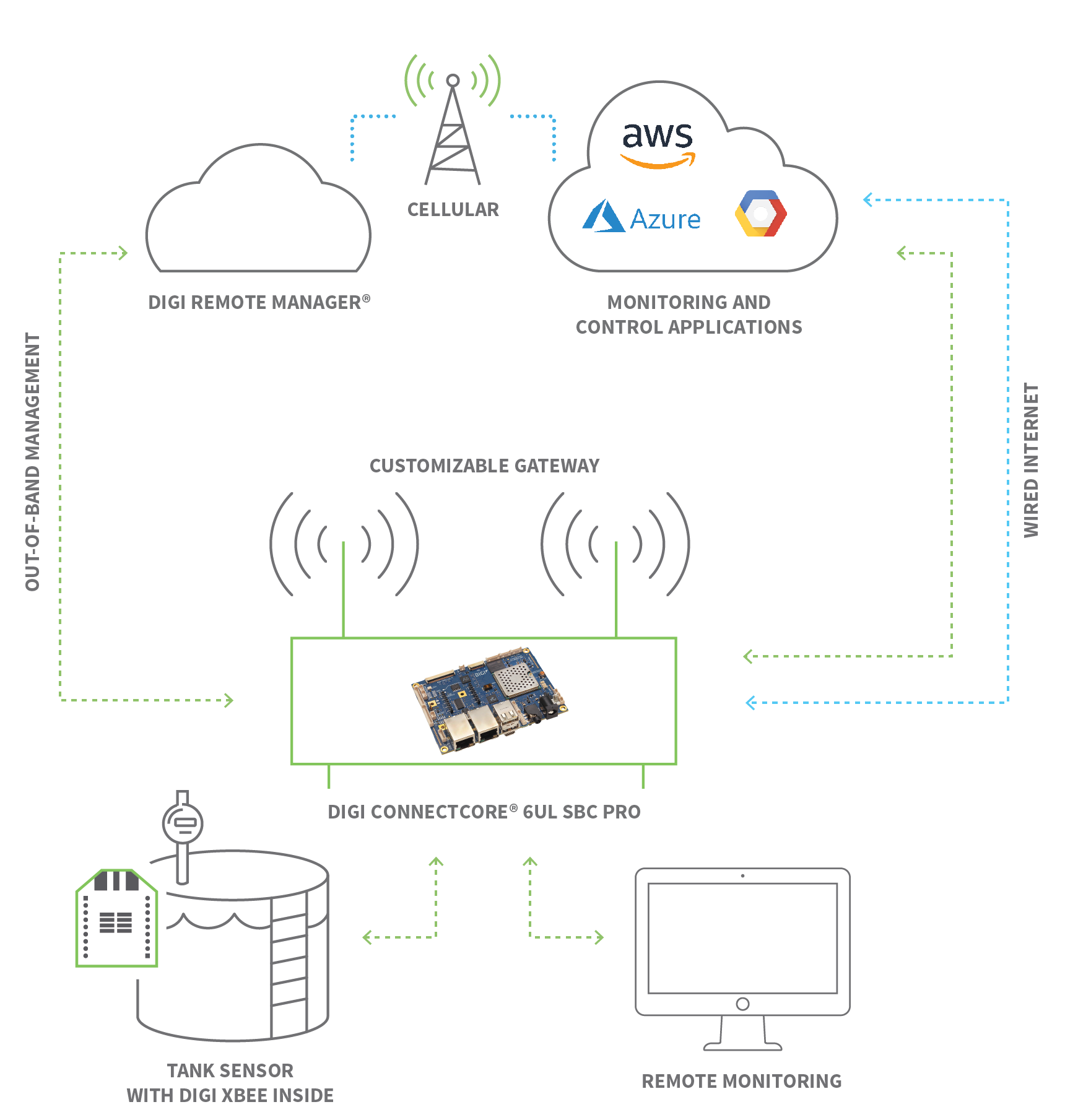
Before delving into the specifics, it's crucial to understand the foundational elements. A compatible IoT device is the first requirement. This could range from a simple smart home appliance to sophisticated industrial sensors. Equally vital is a stable internet connection, which acts as the gateway to your connected devices. Furthermore, the choice of remote access method will significantly influence your experience, offering varying levels of security, ease of use, and functionality. For instance, the remote IoT platform provides a user-friendly interface through a web browser, while Virtual Network Computing (VNC) allows for direct interaction with a device's graphical user interface (GUI), mirroring the desktop experience. These diverse approaches cater to different needs and preferences, ensuring that remote access is accessible and effective for a wide audience.
- Josh Allen Sean Mcdermott Contracts Salaries Bills Future
- Sarah Simpson The Woman Behind Sturgill Simpsons Success Learn More
To understand this transformative technology, consider the following data:
| Aspect | Details | Relevance |
|---|---|---|
| Definition | Remote access to IoT devices refers to the ability to control, monitor, and manage internet-connected devices from a distance, typically via a network connection such as the internet. | This capability allows users to interact with their devices from anywhere with an internet connection, providing unparalleled convenience and efficiency. |
| Key Technologies | VNC (Virtual Network Computing), SSH (Secure Shell), Web-based platforms, Mobile applications (e.g., Arduino IoT Remote). | Different technologies cater to various needs, offering features like GUI access (VNC), secure command-line access (SSH), and platform-specific dashboards. |
| Prerequisites | A compatible IoT device, a stable internet connection, and appropriate software or platform for remote access. Security protocols and proper device configuration are crucial. | These form the foundation for establishing and maintaining a reliable and secure remote connection. |
| Benefits | Enhanced efficiency, automation capabilities, the ability to monitor and manage devices from any location, remote troubleshooting and maintenance, and improved resource utilization. | Significant improvements in operational efficiency, reduced downtime, and cost savings are major benefits. |
| Use Cases | Smart homes (temperature control, security systems), industrial automation (equipment monitoring, predictive maintenance), logistics (asset tracking), and environmental monitoring. | Remote access is applicable across various sectors, increasing the convenience and management of IoT devices. |
| Security Considerations | Implementing robust security measures is paramount. This includes using strong passwords, enabling encryption, and utilizing secure protocols like SSH or VPNs. | Secure access is critical to protect the sensitive data from malicious actions and ensures privacy and integrity. |
| Implementation Methods | Direct methods using device and service SDKs, platforms like Azure IoT Hub, or specialized solutions such as TeamViewer Tensor. | Different strategies can be chosen according to the complexity of the applications and the needs of the users. |
| Future Trends | The integration of IoT with AI and cloud computing and increasing focus on secure access and more efficient network management. | This technology is in constant development and aims for improving the performance and the ability to automate processes. |
| Reference Link | Example IoT Remote Access Guide | Provides additional information and resources for further learning. |
For those managing multiple IoT devices, centralized management platforms offer a streamlined approach. These platforms serve as a central point of control, allowing administrators to monitor and manage various devices efficiently. Platforms like Azure IoT Hub provide tools to manage IoT devices from the cloud and ingest high volumes of device telemetry. This unified experience simplifies device management, providing a more intuitive and integrated workflow.
Different methods exist for remotely accessing IoT devices, each with advantages and considerations. VNC, for instance, offers a way to safely access the graphical user interface (GUI) or desktop of a device. By setting up a VNC server on a device like a Raspberry Pi and utilizing a VNC client application on a device of choice, users can interact with the device's desktop from anywhere with an internet connection. This method is particularly useful for devices that require direct visual interaction or desktop-based control. Consider it an accessible gateway to your devices, bridging the physical and virtual realms.
For more technical users, remote SSH (Secure Shell) access offers a powerful and secure method for monitoring and managing IoT devices. SSH provides a secure, encrypted connection, making it ideal for remote monitoring, management, and troubleshooting. SSH is commonly used for remote monitoring and management of devices and is an ideal choice for secure access. AWS IoT Device Management offers secure tunneling, which helps in remote tasks by establishing a secure connection managed by AWS IoT. This approach reduces the need for updates to your firewall rules, adding another layer of security. Setting up an SSH connection requires a stable internet connection, proper configuration of the IoT device, and appropriate security protocols.
Wireless methods for connecting IoT devices may seem convenient, but they often have downsides. While these options provide ease of use, they can compromise security and reliability. The method you choose should therefore align with the specific security needs and the environment in which you operate.
The Arduino IoT Remote phone application provides another approach, letting you control and monitor your dashboards in the Arduino Cloud. With the app, you can access your phone's internal sensors, adding another dimension to your IoT control. It offers features such as GPS data, light sensor information, and IMU data, expanding the functionality of your IoT projects. This integration offers seamless control and real-time monitoring capabilities.
For professional or industrial settings, where sensitive data is handled or direct remote access is required, VPNs are often the preferred solution. VPNs provide a secure and encrypted connection between devices, ensuring that data transmitted remains confidential. Professionals can utilize VPNs to securely access IoT devices on remote networks, especially when ensuring safe communication between devices operating on distinct networks is important. Using device and service SDKs can also be a powerful means to implement remote access, which typically starts with the service client of the service SDK and utilizes the service connection string. This approach allows you to initiate a connection request to an IoT device through the `createstreamasync` method.
Web dashboards are also important when dealing with remote control of IoT devices. They present a user-friendly interface for monitoring and managing your devices, providing a clear overview of their status and performance. These dashboards offer a seamless way to visualize device data, control device functions, and customize the functionality of connected devices. These user-friendly interfaces offer accessibility and make it easy for users of all technical backgrounds to manage IoT devices remotely.
In the world of IoT, the benefits of remote access for enterprises are manifold. It enhances logistics, helps optimize supply chains, and improves automation processes. Remote access capabilities offer a way to maintain performance while cutting down on costs and maximizing efficiency. The deployment of IoT technology in the global supply chain market is forecasted to grow significantly, emphasizing the importance of remote access and management. In essence, remote access is a critical enabler for achieving the full potential of IoT across various industries.
Ensuring the security of your remote connections is paramount. Use strong passwords, enable encryption protocols, and implement multi-factor authentication where possible. Regularly update the software and firmware on your IoT devices to patch security vulnerabilities. Always assess your network configurations and limit access to your devices to only authorized users and devices.
Centralized management platforms are great but it's equally crucial to adopt centralized management platforms. From this vantage point, you can gain control over the entire system and streamline operations. You must choose the right platform, and take the necessary steps to ensure device functionality. Strategies for acquiring remote management solutions must be well-thought-out.
In conclusion, the ability to remotely access IoT devices is more than a technological advancement; it is a paradigm shift in how we interact with the world around us. Whether through a web browser, a mobile application, or a secure SSH connection, the possibilities are endless. By understanding the available methods, considering security implications, and choosing the right approach for your needs, you can unlock the full potential of this transformative technology and harness the power of remote control. Remember that remote access is a powerful tool, and it is your responsibility to utilize it securely and effectively.
Article Recommendations
- Bhad Bhabies Hottest Content Videos Leaks Mustsee
- Sarah Simpson The Woman Behind Sturgill Simpsons Success Learn More


Detail Author:
- Name : Mrs. Dariana Haag III
- Username : angela.hudson
- Email : brent.mueller@hudson.com
- Birthdate : 1993-02-17
- Address : 907 Kuhlman Alley Apt. 367 Goodwinberg, ME 55903
- Phone : 786-756-1592
- Company : Jast, Windler and Weimann
- Job : Construction Manager
- Bio : Iure minima earum eligendi ut qui nam. Culpa autem asperiores nesciunt neque vero. Ab ut est voluptatem voluptatem quod. Saepe velit voluptas illo praesentium qui.
Socials
linkedin:
- url : https://linkedin.com/in/jean.purdy
- username : jean.purdy
- bio : Dolorem possimus ea qui qui quo beatae.
- followers : 6239
- following : 2936
facebook:
- url : https://facebook.com/jean_purdy
- username : jean_purdy
- bio : Laudantium quibusdam nesciunt quidem autem in labore.
- followers : 6846
- following : 677
twitter:
- url : https://twitter.com/jean_dev
- username : jean_dev
- bio : Aut aut aut qui suscipit at molestiae modi. Expedita dolor dolores quia pariatur voluptates et dolores id. Adipisci ab dolores nulla omnis autem quia.
- followers : 4063
- following : 2789